Backtrack 101-2-Dirbuster
Backtrack 101 Series aims to introduce beginners to tools distributed with Backtrack Linux. Thus, according to these articles, a beginner can more easily participate in hackfest games and start learning about penetration testing.
In this first article, we will talk about a practical tool named Dirbuster.
Official website of the project: https://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
Synopsie:
Dirbuster is a free Java application distributed by the OWASP group. The aim of the tool is to discover hidden directories and files on a web server. In fact, many programmers and administrators have tandance to hide pages and critical sections by not binding files and directory on their website. Using a tool like Dirbuster, it is possible to locate these files and directories.
How it works?
Dirbuster can operate in two modes:
- Dictionary attack
- Brute Force
In the first case, a word list will be used to query the target website. This limits the queries only to the words in the list. In the event that this is not sufficient, it is possible to use brute force mode in which all possible word will be tried. Unfortunately,brute force mode significantly increase the time required to make a discovery and also increases the trace of the program on the network. Thus, when an attempt is made with a word, regardless of the method, the result of the query is parsed by the application. In the event of a successful query, the program indicates that it has discovered a directory or file.
List of words
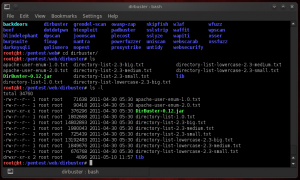
Fortunately for us, Dirbuster is distributed with 9 word lists prepared by the team of OWASP. These lists are available in the directory /pentest /web/dirbuster as shown in the following figure:
Bases
With these word lists, you are ready to use Dirbuster. To launch the application from the command line, inside the directory Dirbuster, you can control:
root@bt:/pentest/web/dirbuster # java -jar Dirbuster 0.12.jar
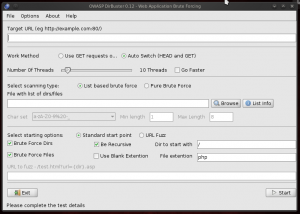
Dirbuster application should open as shown in the next figure:
We are now ready to use the application. The purpose of the article, I have prepared a web server with a hierarchy in order to make tests. Here is the listing of files present in the web server organized to see the files in the directory:
LISTING FILE ON THE SERVER
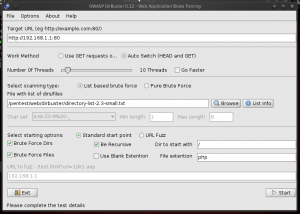
To start, we will use the default settings of the application by selecting the desired target (192.168.1.1 in my case) and the directory-list-2.3-small.txt word list (you can learn more about the organization lists of words on the official website of the project already quoted at the beginning of the article). Before running the tool, the interface should look like this:
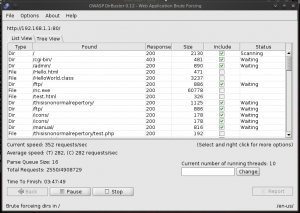
By pressing the Start button the tool is launched and the dictionary attack begins. As running the tool can be quite long, it is possible and very convenient to see live search results while it is in progress. The following figure shows the tool in action:
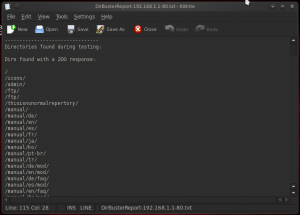
When the process is completed, or when you shut it, it is possible to save the findings in a report, the following figure shows a small part of the report on the test environment:
As the report shows, it is possible to learn that a directory that was not listed was discovered. In fact, the manual directory is added by apache server used for this demonstration. A quick visit to the directory as you can see in the following figure the directory is actually available on the web server.
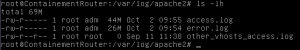
Thus, using this approach we can learn a lot of informations about the files and directories on the server. Unfortunately for the attacking side, this method of discovering hidden files and folders on the server leave heavy traces in web server log as shown in the following figure.
Do not forget that this server is only used for this example. Log files 44 MB and 26 MB are definitely annormal. A simple routine monitoring may allow the discovery of the incident by inspecting the server logs.
Some additional options
Brute force
From the main interface, it is possible to select, as shown in the following figure, to use the brute force method. When this mode is enabled, the application stops using a word list and tries all possibilities. This mode can be useful if what you're looking for is not in the word lists.
URL Fuzz
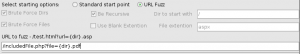
From the main interface, you can select the URL Fuzz. This mode is useful for testing, for example, file inclusions made within URL. The following figure shows how to use this mode.
In the example given here, the inclusions file is a parameter used when calling the file includeFile.php sometimes, this can be used to discover files not served by the server. Note that with a list of appropriate word, it would be possible to use this tool fuzzer for a lot of things.
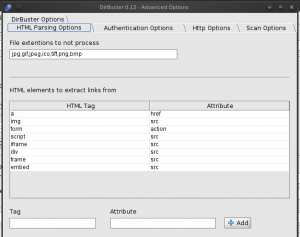
HTML Parsing
By default, the interpretation of HTML is enabled. The interpretation of HTML tags can be configured in more detail. The interpretation options are available from the advanced options available through the menu options of the application. Here is the configuration interface:
As you can see, it is possible from this interface to specify html tags and attributes to be parsed. Thus, it is possible to discover files and folders by inspecting the parameters of HTML tags. Example, we could add the link tag which is normally used to include css files.
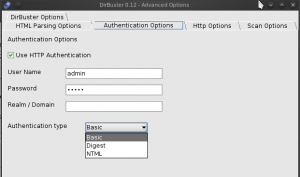
Authentication Options
Dirbuster also offers authentication management. Thus, using the authentication options, it is possible for Dirbuster to enter within password protected directories. Authentication options are available from the advanced options available through the menu options of the application. As shown in the following figure, the activation of these options is simple. Simply activate the check box, enter the credentials and select the authentication mode.
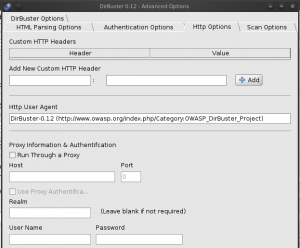
HTTP Options
Some options of the HTTP protocol can be configured to modify the behavior of the application. HTTP options are available from the advanced options available through the menu options of the application. It is in this interface it is possible to configure a proxy if necessary. In addition, it is also possible to set custom HTTP headers as needed. An important feature is the User Agent configuration. Some sites could detect the use of Dirbuster using his user agent and thus refuse requests from the tool. An attacker could then modify the parameter value by using a browser User Agent and thus prevent a server to block Dirbuster requests based on the User Agent. The following figure shows the configuration interface options HTTP.
In the end
As we have been able to see, using Dirbuster could be part of an early step in a penetration test on a web server. Unfortunately, the footprints it leaves on the server, although limitable (scan option not discussed in the article) still remains important and relatively easy to detect.
You like this article?
You would like to read an article about a tool that you do not familiar with? Just let the tool name in comments, if available in Backtrack, an article will be written about the tool.
Backtrack 101 Series aims to introduce beginners to tools distributed with Backtrack Linux. Thus, according to these articles, a beginner can more easily participate in hackfest games and start learning about penetration testing.
.